With the current standing of cybersecurity, threats of data breaches are a constant and costly concern. It is vital that organizations search for the most all-encompassing frameworks to fortify their data. The National Institute of Standards and Technology (NIST), part of the United States Department of Commerce, is a leading authority in shaping these standards. The NIST Special Publication (SP) 800-53 Rev. 5 control families serve as a beacon of excellence in research and development.
In a continuous effort to improve data security regulations, NIST developed the comprehensive NIST SP 800-53 framework. Serving as a cornerstone for countless organizations, this framework sets the standard for security controls and guidelines, offering a roadmap toward resilience against digital threats.
About NIST SP 800-53
The NIST SP 800-53 framework is a compliance standard mandated for federal information systems, government agencies, and affiliated contractors. This framework ensures comprehensive security measures are in place, promoting the safety of federal organizations and validating the security efforts of third-party vendors and partners.
While the NIST SP 800-53 framework is required for federal entities, its versatile foundation makes it a great framework for all organizations. The framework divides security controls into twenty families that include different areas of focus. These focus areas range from employee awareness and training to specific configuration management.
Some of the NIST framework’s key strengths are adaptability, accessibility, and cost-effectiveness. By refraining from endorsing specific tools, companies, or vendors, the framework remains relevant amidst evolving technologies, systems, environments, and organizational changes. This flexibility enables organizations to address emerging cybersecurity challenges effectively, ensuring continued resilience in the face of evolving threats.
Obtaining the NIST 800-53 framework is also cost-effective, as it is available free of charge, unlike many other frameworks. This accessibility makes it a particularly attractive option for organizations seeking comprehensive guidance on securing their data. Providing this framework at no cost enables a broader range of organizations, regardless of size or budget constraints, to leverage its valuable insights and recommendations for enhancing their security posture.
The transition from NIST SP 800-53 Revision 4 to Revision 5 marks a significant milestone in the framework’s evolution. This comprehensive update focuses on enhancing cloud environments, updating controls, and incorporating advanced technology to remain secure and relevant against evolving threats. As a result, organizations can leverage the latest version of the NIST SP 800-53 framework to bolster their cybersecurity posture with greater assurance and effectiveness.
Top NIST Controls
Every control within the NIST SP 800-53 Rev. 5 control families receives a score from the MITRE ATT&CK Framework, indicating their significance and impact on an organization’s cybersecurity posture. While the MITRE ATT&CK framework is not a part of the core NIST publication, the scores are given by professionals who use past experiences to inform future cyber threat detection and mitigation. The score of a control correlates with its importance. The higher ratings signify a greater impact on an organization’s overall cyber posture. The following NIST SP 800-53 Rev. 5 control families include controls with some of the highest MITRE ATT&CK impact scores.
Configuration Management (CM)
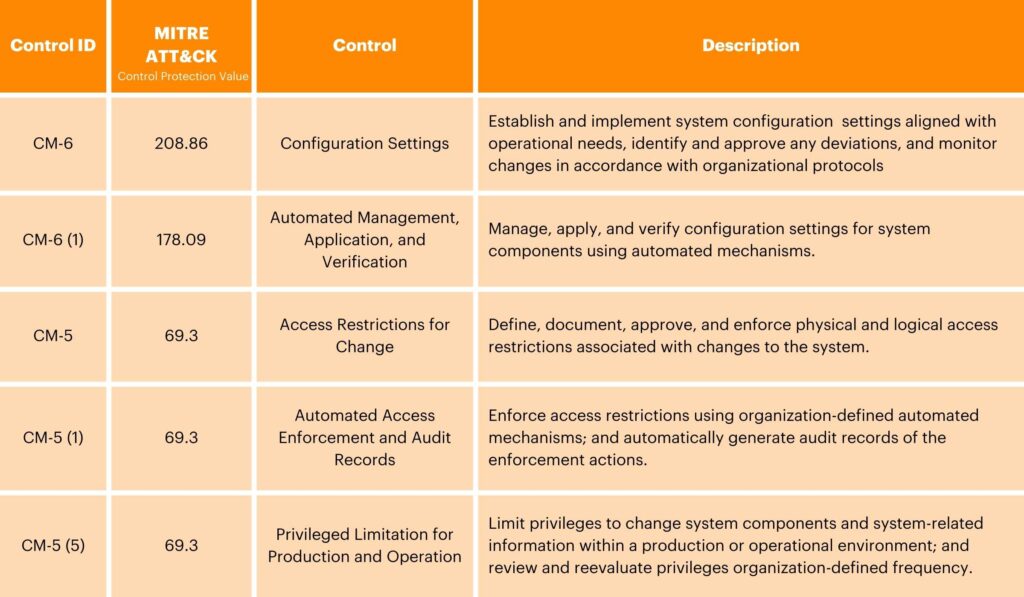
The Configuration Management control family encompasses a set of controls aimed at effectively managing updates to system configurations while establishing the best policies for authorized software usage. Implementing this set of controls aims to govern configuration changes, ensuring that only authorized modifications are made to system settings, software, and related components. These types of controls also define and enforce policies that dictate which software applications are permitted within the organization, ensuring security requirements and operational needs are aligned. Through these measures, Configuration Management aims to maintain system integrity, stability, and security while facilitating efficient software management practices.
Identification and Authentication (IA)
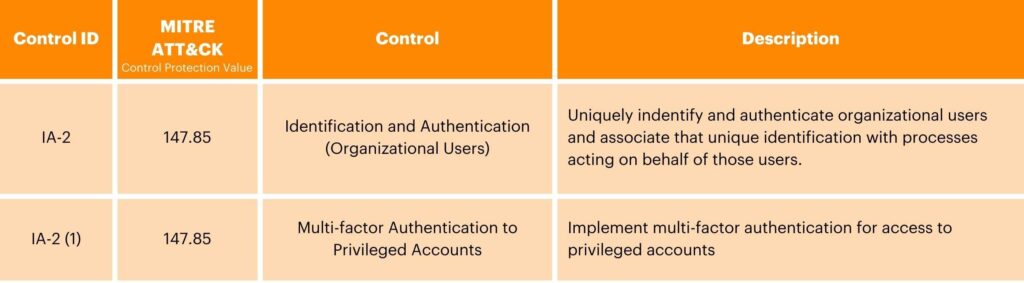
The Identification and Authentication control family covers a range of controls aimed at effectively managing user, device, and service credentials, as well as establishing robust authentication policies and systems. This involves implementing strategies to accurately identify users, devices, and services accessing the system; typically using usernames, passwords, digital certificates, or biometric data.
This control family also encourages setting authentication policies to define the requirements and methods for verifying the identity of entities attempting to access the organization’s network. These policies might incorporate multi-factor authentication or alternative authentication methods.
System and Information Integrity (SI)
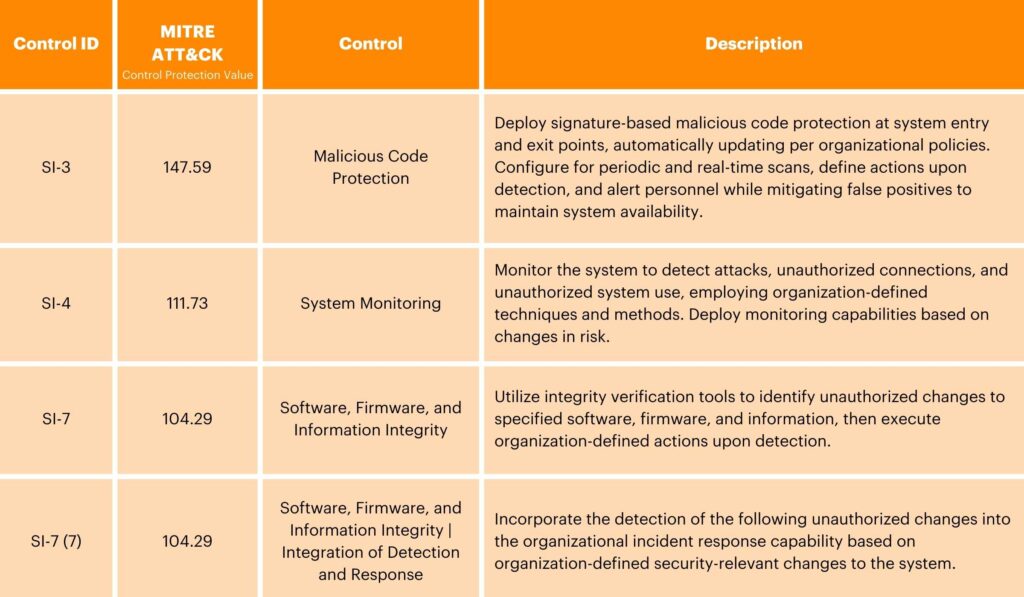
The System and Information Integrity control family advocates for the execution of proactive measures to ensure the security and integrity of organizational systems and information. This involves implementing monitoring systems to track system activities and network traffic, while also promptly alerting potential security incidents if they occur. Organizations are also encouraged to establish effective flaw remediation processes, including regular application of security patches, vulnerability assessments, and configuration management practices. By adhering to these controls, organizations can enhance their cybersecurity posture and mitigate the risk of unauthorized access or data breaches.
Access Control (AC)
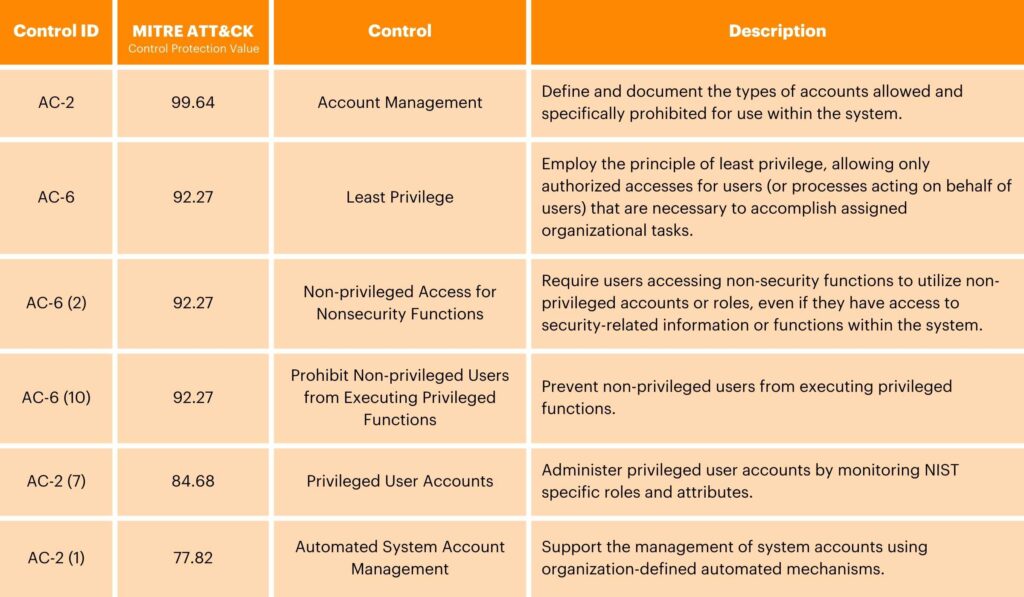
The Access Control family emphasizes controls that manage your organization’s user accounts and monitor activities within organizational information systems, promoting the principles of least privilege and separation of duties. By only granting users the necessary access for their position and distributing responsibilities among different roles, organizations can reduce the risk of unauthorized access and potential misuse of sensitive data. Implementing effective account management practices, such as password policies and regular access reviews, helps to ensure alignment with security requirements and business needs.
Audit and Accountability (AU)
The Audit and Accountability family stresses the importance of record-keeping and analysis within organizational frameworks. It prompts organizations to conduct comprehensive audits of their records and content, ensuring thorough examination and documentation of system activities, transactions, and events. By meticulously documenting and analyzing system activities, organizations gain valuable insights into operational efficiency, security posture, and compliance adherence. The ability to generate insightful reports based on audit findings allows for data-driven decision-making which empowers informed strategies for risk mitigation, process improvement, and regulatory compliance. Adherence to the principles outlined in the Audit and Accountability family is critical for fostering transparency, accountability, and data-driven decision-making within organizational contexts.

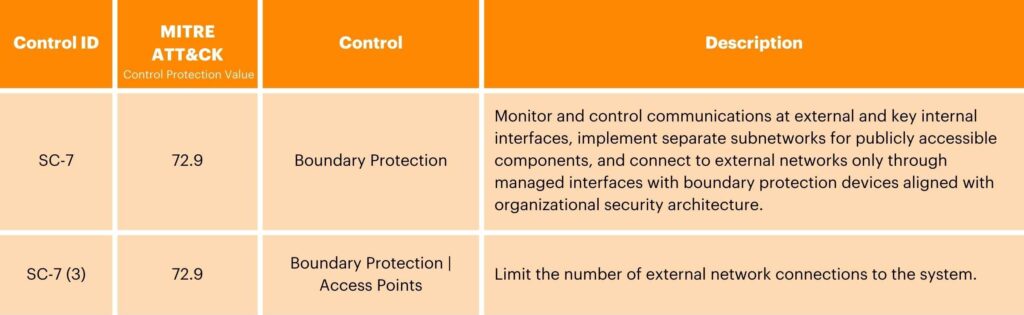
System and Communications Protection (SC)
The System and Communications Protection control family encompasses critical controls aimed at enhancing the security and reliability of organizational systems and communication channels. These controls prioritize the segmentation of applications and systems to contain potential breaches and limit their impact. These controls also focus on securing passwords and other sensitive information through the enforcement of strong authentication and access control mechanisms, including stringent password policies and encryption protocols. By adhering to these measures, organizations can mitigate the risk of unauthorized access, data breaches, and eavesdropping attacks, thereby fostering trust, ensuring compliance, and safeguarding sensitive information assets.
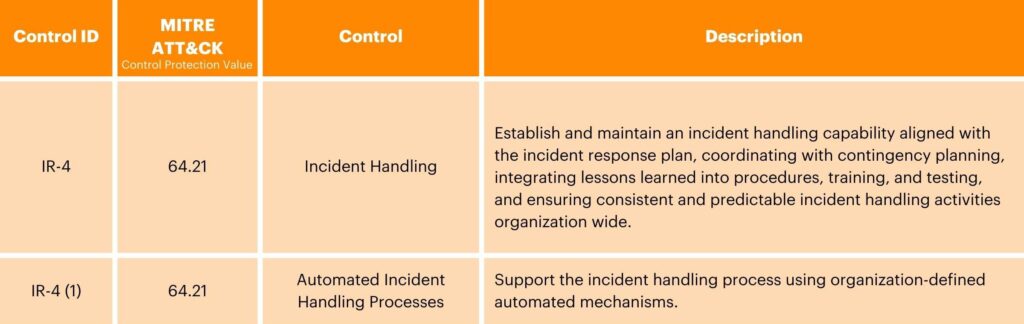
Incident Response (IR)
The Incident Response control family is dedicated to improving organizations’ incident response protocols and resources. It promotes the implementation of rigorous incident response training programs to equip personnel with the necessary skills to detect, assess, and respond to security incidents effectively. With controls in this family, organizations are encouraged to set up monitoring and reporting systems, leveraging advanced technologies to continuously monitor network activity and promptly detect anomalies or security breaches. Reporting mechanisms help to facilitate the quick escalation of suspected incidents to designated response teams, enabling coordinated action to mitigate risks and minimize potential damages.
Leverage Expertise for NIST Control Complexities
Navigating the extensive controls and standards within the NIST SP 800-53 Rev. 5 control families can seem overwhelming when trying to achieve true data protection. The first step towards achieving this goal involves creating a cybersecurity strategy. This strategy will include identifying organizational requirements, educating your organization on the NIST SP 800-53 Rev. 5 control families, conducting thorough gap analyses, and implementing industry best practices. Collaborating with cybersecurity consultants can streamline this process, as they leverage their expertise to assess an organization’s security posture and tailor a customized strategy accordingly. Recognizing that data protection is a continuous journey, rather than a fixed destination, partnering with experienced professionals can prove invaluable in navigating and optimizing cybersecurity efforts.
Partner with our Cybersecurity Consultants Today
By emphasizing the importance of strategic cybersecurity planning and collaboration with experienced consultants, organizations can effectively navigate the complexities of compliance and bolster their security posture. With the recent transition to Revision 5, the framework has further solidified its relevance and effectiveness in safeguarding sensitive data and critical assets. As organizations continue their journey towards data protection, leveraging the guidance and resources offered by the NIST SP 800-53 framework remains essential in ensuring resilience against cyber threats and maintaining trust in today’s digital landscape.





